At a time when the use and manipulation of data is mushrooming, the threats from cyber breaches and fraud is similarly exploding leading to more stringent obligations from regulators on the use and protection of personal data.
The information above is from the Cyber Security Breaches Survey, April 2018 by Department for Digital, Culture, Media and Sport.
The threats of data security breaches and fraud come three principal sources:
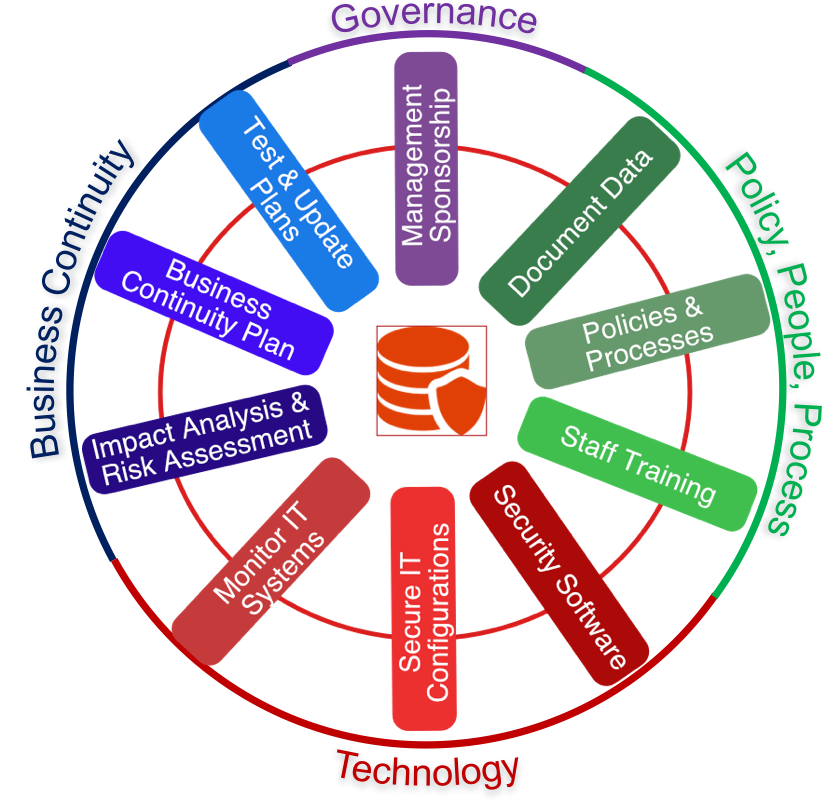
Accordingly, protection from these threats need to be addressed across policy, process, people and technology with the lead and direction coming from senior management. Read our blog on creating as systematic approach to cyber security.
Read on to learn how we can help bolster your security
We have a comprehensive approach to securing your business that we describe in a "Cyber Security Wheel".
You may pick and choose the elements that are important to you and progress around the wheel at a time that suits you.
We can assist with IT Security Policies, staff training, secure software and configurations.
Even fully protected organisations may still suffer a cybersecurity breach, and so increasingly organisations are developing incident recovery plans to minimise the impact of attacks. Our "Wheel" has this capability of one of its attributes.
ESET’s award winning malware detection and protection for your business. Every workstation and endpoint needs protection, with ESET Endpoint Security and ESET Remote Administrator you can easily implement and maintain a powerful anti-malware solution.
Antivirus and Antispyware combats all threats, including viruses, rootkits, worms and spyware. Optional cloud-powered scanning allows whitelisting of safe files based on a file reputation database in the cloud, ensuring better detection and faster scanning. Filter and scan incoming emails for spam, malicious attachments and other content, with native support for Microsoft Outlook. ESET’s Two-Way Firewall works to protect against external intrusion, particularly when using unsecure public Wi-Fi: essential for a mobile workforce.
ESET’s signature low system footprint ensures that your hardware runs faster for longer. A small update package keeps you protected against the latest threats without consuming all of your bandwidth. Prevent threats being brought into the company physically with Device Control, allowing you to block unauthorised CDs/DVDs and USBs.

Data is an integral part of modern business. When data is moved from place to place, whether it’s via the internet or physical storage, it is vulnerable - something that recognised in the GDPR.
Proactively protect your data with ESET Endpoint Encryption to increase user GDPR compliance and the security of your company data
Full disk and removable media encryption keeps your data safe on the road. File, folder and email encryption keeps any collaboration across your established workgroups and teams secure; with your security policy enforced at all endpoints by the Endpoint Encryption Enterprise Server.
Manage users and workstations together or independently with the Endpoint Encryption Enterprise server. Keep your most high-risk endpoints under close control at all times: activation and changes to security policy, software feature-set, encryption keys and endpoint status are all handled securely through the cloud to simplify control. Only Endpoint Encryption offers full control wherever your users are allowing employees to work from home or on the move whilst enjoying the full protection of Endpoint Encryption.

For 30 years, ESET® has been developing industry-leading IT security software and services for businesses and consumers worldwide. With solutions ranging from endpoint and mobile security, to encryption and multi factor authentication, ESET’s high-performing, easy-to-use products give users the peace of mind to enjoy the full potential of their technology.
We have partnered with ESET for 10 years - since our business started. They provide great software that protects our customers devices and the software runs with a small footprint - so it doesn't disrupt your daily work.
What's equally important is the great support ESET provide us when we need help. So when you have a complex issue, ESET is right there to back us up.
Firewalls are network security devices that monitor incoming and outgoing traffic and decide whether to allow or block specific traffic based on a set of security rules.
They establish a barrier between secured internal networks that can be trusted and untrusted outside networks, such as the Internet. Filters need to be configured that determine which packet are allowed to go where.
Firewalls can be hardware, software, or both and are often built into other products.
We use firewalls from Dreytek and TP Link included with their routers.
ESET endpoint security software also includes a firewall capability enabling indiviual devices to be protected.

Did you know:
* On average, UK citizens have 22 passwords each;
* The number of websites for which users have the same password is 4;
* Only 44% of users change their passwords each year;
* 35% of users forget their passwords each week.
So how do you keep all your business applications secure, ensure your users apply sensible passwords and change them regularly?
Welcome to password managers.
Software that helps you set and remember passwords and keep them secure. With a password manager you only have to remember one secure password and the password manager stores and remembers the rest.
We recommend MyKi:
*Works across devices – PCs, Macs, Smartphone and Tablets
* Works across teams – allowing teams to share information
* Stores passwords in a secure vault
* Autofills every password
* Generates random passwords
* Audits your passwords
In addition, Myki also works as a 2 Factor Authentication App - 2 in one!
We use MyKi at PAAC IT to secure access to our systems.
