“It wont happen to me”
“It’s unlikely to happen to me” or “It only happens to big companies” are two of the biggest push backs we receive from small businesses about protecting themselves from information security breaches. Unfortunately, it most probably will – a survey conducted earlier this year found that 43% of small businesses and 19% of charities suffered a cyber breach or attack in the past 12 months. Despite these worrying statistics many organisations are unprepared:
- Only 26% of micro/small businesses have formal cyber security policies
- Only 19% of micro/small businesses have cyber security training
- Only 18% of small businesses have cyber security incident response plans
- Only 37% of businesses have rules and controls around encryption – although this is recommended in the GDPR
- 48% of small businesses don’t follow software and app updates cyber advice.
Yet the impact can be significant with 89% of small businesses experiencing a reputational impact following a cyber attack – the cost is more than financial.
In this blog we look at systematic approach to securing your business from a data breach – whether accidental or malicious.
The GDPR requires appropriate technical and organisational measures
As an additional incentive to get serious about information security, the GDPR require organisations that process personal data to implement appropriate technical and organisational measures and be able to demonstrate that processing is performed in accordance with the regulations. The fines are very considerable for non-compliance and / or experiencing a data breach – up to €20m – eye watering.
Our Systematic Approach to Information Security
A systematic approach needs to be led and driven by one of the organisation’s management team and reach out across the organisation. Our approach is founded on the information security guidelines from the National Cyber Security Agency.
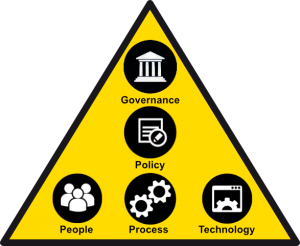
The top down layered structure works down and across the organisation:
- Governance: led by a senior director to ensure guidance and direction from the top;
- Policies: to provide the intent, principles and rules regarding data security to staff and technology providers to follow;
- Procedures: to translate the policies, where required, into instructions and guidelines to follow;
- People: All staff working for and in the organisation and
- Technology: your computer systems, networks and data storage that need to be configured and operated in accordance with the security policies.
Lead from the top with a governance team
An Information Security Governance team should meet regularly to set and manage direction and the implementation of data security matters. We suggest the team members could be:
- A Director or another senior board level representative;
- Your Data Protection Manager or Officer;
- Your Office Manager or a person that deals with operational processes, which may be formal or informal; and
- An IT representative – could be an internal person or a senior person from your IT Services Provider.
The mandate of the Information Security Governance team is to ensure the security of your information and to provide the central response focus and leadership in the case of a data breach.
Policies are needed to set the business intent
The intent of the governance team should be expressed through a set of security policies that cover two main areas:
- The set of polices covers areas such as data protection, acceptable use of IT, email, social media and the internet, workstation security, access control to IT systems, the use of WiFi and GDPR related policies;
- IT systems and information management: Policies cover all aspects of IT management and security including monitoring, firewalls, security and encryption software, workstation build, software and cloud services, information storage and backup and WiFi networks.
Processes to institutionalise policies
A number of processes need to incorporate cyber security issues with three key ones being:
- IT security awareness training for new joiners;
- Exit management of leavers to ensure access privileges are revoked; and
- Data breach management process.
Create a “human firewall” by training your people
A Willis Towers Watson survey discovered that 58% of cyber claims are attributable to employee behaviour. Which could be either through negligence, accidental disclosure and lost or stolen devices. This is borne out by the most commonly reported data beaches to the Information Commissioners Office (ICO):
- Data posted or faxed to the incorrect recipient;
- Loss or theft of paperwork;
- Data sent by email to incorrect recipient;
- Failure to redact data and
- Failure to use BCC when sending email.
How much do your staff know and how aware are they of the dangers?
So cyber security, just like data protection, should be a part of day to day life from the day someone starts with your organisation though to their departure:
- Staff should go through a thorough pre-employment check and be required to sign a confidentiality agreement as part of the employment terms and conditions. Further, new staff should be provided with information security training as part of the induction process;
- Provide regular training and updates to staff on data protection, the GDPR and keeping information safe; and
- Your staff exit process should ensure that any IT assets are recovered from leavers and access privileges revoked.
Develop a comprehensive plan to secure your technology
Finally, we come to technology – a place where many organisations start…. and end.
The key points relating to security of your computer systems are:
- User access control. Access to systems should be managed at multiple levels with access being provided on a “need to know” basis. Administrator access should be restricted to a few individuals that need access. A password policy (including regular password changes) should be in place for all users and multi-factor authentication should be employed on critical systems;
- Backups. Ensure you backup data regularly to a secure environment – preferably offsite. Backups may be your only defence against ransomware attacks;
- Secure configurations. You should change passwords from default settings and unused or not-needed software should be removed from devices;
- Security Software. Protect workstations and servers by endpoint security software. Ideally, security software should be centrally managed to ensure it remains current and to enable a rapid reaction to any detected incidents;
- Portable and mobile devices. You should secure laptops, tablets and smartphones with passwords, PINs fingerprint or face recognition technologies. It is strongly recommended to use encryption software on portable devices;
- Software Management. Workstation operating systems should be set to automatically update with security patches as they become available. Only approved and business relevant software should be installed on your devices;
- Firewalls. Activate firewalls on personal workstations and “perimeter” security is maintained through a firewall often included within edge routers; and
- Monitoring.Continuously monitor computers, networks and software to enable early detection of security issues.
The size of your business is almost irrelevant in developing a cyber security defence plan as every business needs to protect itself. Obviously, the scale and scope will vary, but you do need to cover all the elements – governance, policies, people and technology.
Need help, get in contact or give us a call. 01428 770 290 is the number
The statistics above are from the Cyber Security Breaches Survey, April 2018 by Department for Digital, Culture, Media and Sport