Your data is more valuable to you than to anyone else. That is why hackers are after your data: so they can sell it back to you. They want to prevent you from doing business, in effect holding your business for ransom. All it takes is one click by one employee on an attachment in an email personalised for them, designed to look genuine. To protect your data and systems, you need a well though through multi-layer defensive strategy, similarly to our Norman ancestors with their layers of fortifications.
That one click by one employee begins the process of locking down the employee’s files. In short order, they are prevented from doing their job. Then it silently spreads to other desktops and servers on the network. If left unchecked, it will shut down your business in hours – potentially for days. Your valuable data will be encrypted and marked for deletion unless the ransom is paid.
More and more, ransomware has emerged as a major threat to individuals and businesses alike. Ransomware, a type of malware that encrypts data on infected systems, has become a lucrative option for cyber extortionists. When malware is run, it locks victim’s files and allows criminals to demand payment to release them. Unless you’ve been living under a rock, you are probably well aware that ransomware is a hot topic in the news these days. Organisations of all types and sizes have been impacted, but small businesses can be particularly vulnerable to attacks.
Ransomware is on the rise
In the McAfee Labs June 2018 Threat Report, the number of new ransomware strains saw an increase of 62% in the previous four quarters. This increase brings McAfee’s total number of identified strains to roughly 16 million. According to Carbon Black there more than 6,300 sites on the dark web offering ransomware solutions to carry out your own attack!
Ransomware is distributed in a variety of ways and is difficult to protect against because, just like the flu virus, it is constantly evolving.
There are a few dominant types, or families, of ransomware in existence. Each type has its own variants. It is expected that new families will continue to surface as time goes on. Historically, Microsoft Office, Adobe PDF and image files have been targeted, but now all operating systems, all device types and data stored on premise and in the cloud are all under attack and at risk.
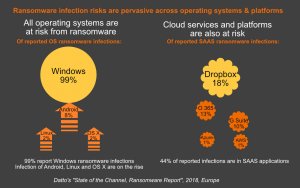
The cost of a ransomware attack is not the payment – it’s the downtime and the recovery effort
IT Service Providers in Datto’s survey of ransomware infections report 21% of SMB clients paid the ransom typically between $500 – $2,000. But of those that paid, 18% never recovered the data. In reality, the impact of an infection is much greater than the cost of the ransom – often up to 10 times more – 62% report loss of data or devices while 78% of SMBs report business threatening downtime while they recover from the infection. Even worse, 11% report malware remained on devices after recovery and struck again!
What should I do – there’s no single answer
Malware most often gets into your systems from spam emails – phishing or spear phishing emails. They trick your users into clicking an attachment or visiting a spoof website. But it can also arrive through users downloading software, from infected flashdrives, from visiting infected websites. In fact almost any seemingly innocuous activity can lead to catching a virus. Some commentators estimate that 70% of infections are caused by your users!
To protect against these various infectious routes requires a multi-layer approach as no one solution will catch everything – and you need a recovery mechanism for when you do get infected. Ive been to Wales recently and visited a number of the old Norman castles – those guys really knew about a multi-layered approach to defence of core assets over 1,000 years ago. We need to adopt a similar well thought out defensive strategy:
- Top of the list is train your users. Teach them to spot fake emails, what to do and who to call if they spot an infection or attack;
- Install a good filtering solution on your emails to cut out fake emails from being delivered in the first place. The filters are out in front, heading off the attack before it reaches your properties;
- Use good quality security software on your devices. Freeware is OK, but OK is not really good enough;
- Ensure you regularly download software patches for your operating systems and key applications to stop malware exploiting vulnerabilities – a bit like ensuring any vulnerabilities in your defences are constantly reinforced;
- Partition your networks to stop infections propagating across devices – like the curtain walls in a castle; and finally
- Backup your files and operating systems so that in the case of an attack you can recover quickly – a option not available in my castle analogy. If you get a ransomware attack, the only reliable way to reliably recover is from a backup. So ensure you practice the recovery process.
Need some guidance – we can help:
- Learn about the backup and recovery services we offer.
- Use our contact form to get to send us a message; or
- Call us on 01428 770 290

